Modernizing Healthcare Networks for the Connected Ecosystem
In this article
Article written by Mark Baik, Information Security Professional - CISSP-ISSAP, CCSFP at Palo Alto
Secure Access Service Edge (SASE) has gained a lot of attention recently as an approach to improve the modern work environment. SASE is now a part of the cybersecurity strategy for many organizations across all industries. The healthcare industry has also embraced SASE, and we're beginning to see health systems and hospitals take interest in building out their SASE architecture. How does SASE help healthcare organizations big and small, and why should healthcare organizations adopt SASE as their modern secure access architecture? What benefits does SASE offer in enabling secure and robust healthcare networks?
Healthcare organizations are undergoing a digital transformation to optimize care delivery and business processes, to quickly adopt new medical technologies and to maximize efficiency while delivering the highest quality of care and services to their patients. Digital transformation is the process of integrating digital technologies into all areas of healthcare delivery, from scheduling and care coordination to managing patient services and medical information.
Decentralization of enterprise resources
Before the widespread adoption of cloud computing, many parts of an organization transitioned to digital processes, and the hospital data center increasingly became the center of the organization. The challenge was to securely connect remote clinics and mobile users to the data center. Dedicated wide-area networks and VPN tunnels connected remote clinics and mobile users to the single source of an organization's digital assets – the data center – while perimeter security products enforced security policies to protect against breaches and malware.
The rapid adoption of cloud computing in recent years has upended this centralized model. The scalability and cost-effectiveness of public cloud services and SaaS applications have caused healthcare organizations to move significant portions of their digital assets out of the on-premises data center and into the cloud and third-party sites. The network perimeter has become less defined, and the traditional data center has become just one of many sources of business-critical applications and data.

Enterprise data, including patient data, is also part of this transition where many healthcare organizations now leverage public cloud infrastructure as part of their storage and backup strategies for business continuity. To enable innovative medical technologies and leverage data analytics, healthcare organizations are sending an increasing volume of medical data to the cloud.
Remote users and devices
The increase of users and devices accessing the enterprise resources from outside the organization's network has also added to the complexity. Although most healthcare organizations have been successful in meeting the increased bandwidth and capacity demands during the pandemic, the organizations have not made an equivalent investment in security to protect the expanded attack surface. The traditional approach of tunneling all traffic from remote employees and devices back to the data center (or wherever the perimeter security stack is) creates inefficient handling of traffic destined for the internet and the cloud resources. This leads to a less-than-optimal user experience. Many organizations, however, still leverage this approach because their network and data security inspection and enforcement capabilities are largely concentrated at the data center.
The traditional approach
Allowing certain traffic to go out directly to cloud resources creates undesired security gaps. Adding multiple point solutions is cost-prohibitive and introduces undesired complexities. Today, more devices, both company-issued and personal, are accessing enterprise resources from outside the network than ever before. COVID-19 certainly played a significant role there. Some organizations needed to relax their security standards to allow employees' personal devices to access enterprise resources from home. With the emergence of telehealth, remote patient monitoring and hospital-at-home services, more IoT and connected medical devices are being sent to patients' homes. These devices need to connect back to an enterprise system and send data for enterprise systems to consume. Protecting those devices and the data they send is a challenge for which traditional perimeter-centric security is not well suited.
This challenge is further amplified by the frequent merger and acquisition (M&A) activities in the healthcare industry today. Non-traditional provider entities, such as the payers and even retail organizations, are entering the healthcare-provider industry, fueling more M&A activities to improve their business viability. Establishing connectivity and bringing these new and acquired remote locations online quickly and securely, while keeping costs down, has become a significant task for larger healthcare organizations. Demand for accessing enterprise resources from these remote locations is rising both on-premises and in the cloud. It's becoming difficult and costly to not only manage bandwidth that relies on expensive private WAN circuits for connectivity, but to also provide required security controls at and between locations.
Although perimeter-centric security offers an effective solution for protecting systems, applications, users and devices that are physically on the healthcare network, organizations need a solution to streamline secure access from remote sites and mobile users that is scalable, resilient and responsive. It needs to scale quickly, even during usage surges, without compromising the user experience. And, it needs to allow users to access enterprise assets securely from anywhere, whether from a remote clinic or employee home, no matter where those digital assets reside. SASE is such a solution for healthcare.
Secure access service edge
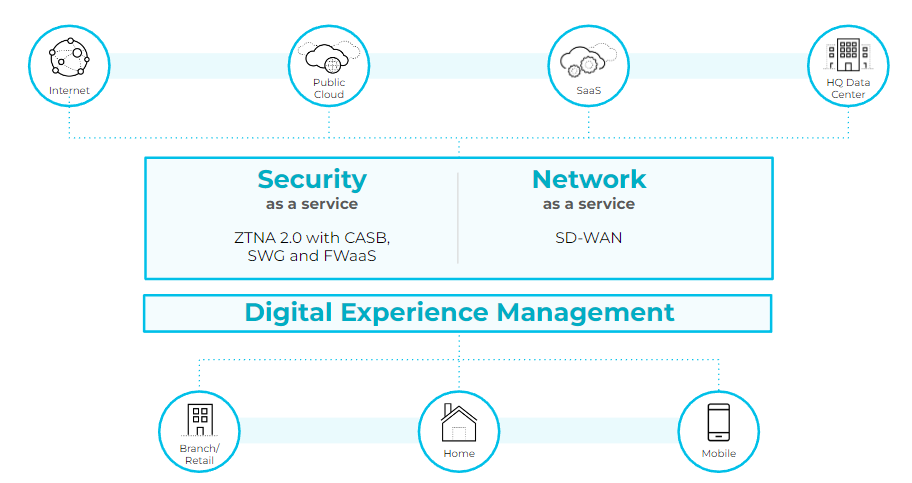
There are many possible SASE use cases for healthcare organizations:
- Zero Trust Network Access 2.0 (ZTNA 2.0) for work-from-home employees and remote clinics.
- Elevating remote clinic performance, security and resiliency.
- Direct internet access for remote clinics, offices and work-from-home employees.
- Improving the digital experience for work-from-home employees, clinicians from remote clinics and patients.
- Optimizing cost-efficiency for WAN connections.
- Comprehensive cloud-delivered security for remote clinics and offices.
- Consolidating multiple security capabilities into a cloud-delivered, single-platform solution.
- Protecting remote patient monitoring and hospital-at-home systems.
- Securely receiving medical data from external medical devices and third-party systems – connections from vendor systems and data from consumer health devices and applications.

